Safeguarding Your Business: An IT Security End-User Checklist

In today’s fast-changing technological landscape, ensuring the security of your company’s sensitive information is critical. IT security needs to be an organization’s top priority since cyber threats are becoming increasingly sophisticated. Furthermore, TASProvider in Richmond Hill, Ontario, understands the importance of data security and has created a comprehensive IT security end-user checklist to assist businesses […]
Navigating Success: How IT Support and MSP Keep Vertical Market Companies on Track

In today’s fast-paced business world, keeping competitive and efficient is critical for companies of all sizes. For businesses in Richmond Hill, Ontario, finding the right IT support and managed service provider (MSP) is akin to securing a compass for their journey toward success. Furthermore, this blog post will look at the critical role that IT […]
Safeguarding Your Smartphone: Essential Tips from TASProvider

In our increasingly digital world, smartphones have become essential tools, holding many personal and sensitive information. Moreover, our smartphones, from confidential emails to financial transactions, are crucial in our daily lives. As reliance on our smartphone grows, so does the need for robust security measures to safeguard our valuable data. TASProvider in Richmond Hill, Ontario, […]
Cloud Security: Everything You Need to Know

Protecting Your Business in the Cloud Businesses increasingly rely on cloud services to streamline operations, improve scalability, and also improve collaboration in today’s fast-paced digital landscape. Furthermore, TASProvider in Richmond Hill, Ontario, understands the importance of cloud computing and cloud security in protecting sensitive data and retaining client confidence as an industry leader. Introduction to […]
What Is Encryption?

Encryption is the process of converting plain text into an indecipherable format. So, the only ones who have access can decode it to the encryption or decryption key. During the encryption process, they encode the data using mathematical techniques. This is the reasons why only a person with the proper decryption key can decode it. They often […]
How to Avoid Having Former Employees Stalk your Company?

There are challenges that small company owners in today’s world must face, challenges associated with conducting business. But it would help if you moved swiftly in other circumstances because the ground collapses under you at every turn. Unfortunately, some of these situations may be rather dangerous for your company, e.g., about your former employees. Why […]
8 Typical Malware Warning Signs on Your PC
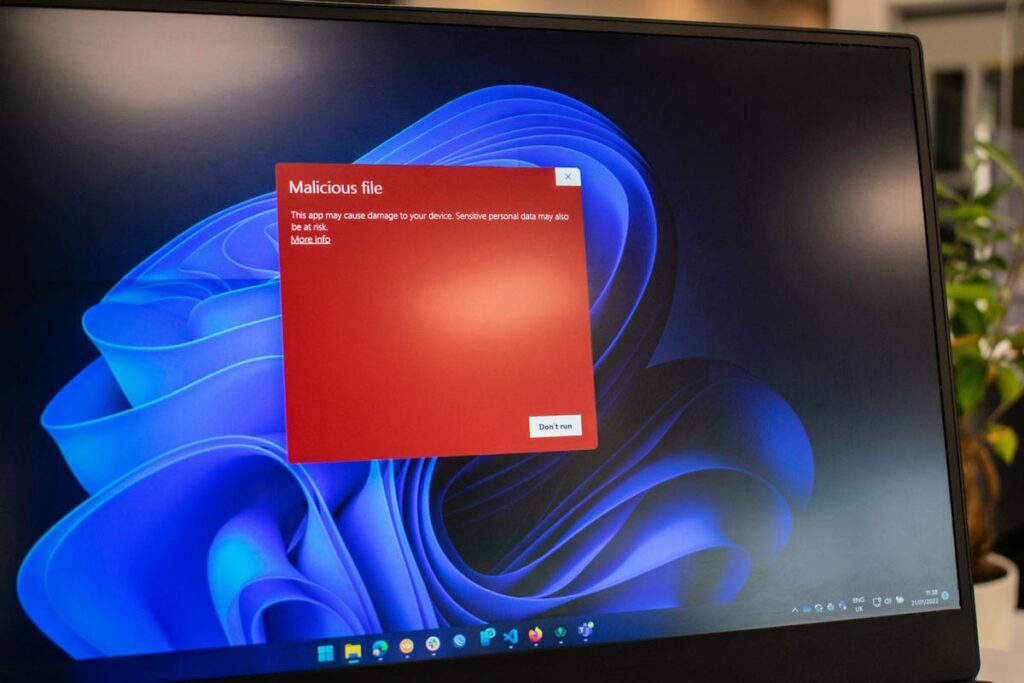
What Exactly Is Malware? Malware is harmful software that silently infiltrates vulnerable consumer devices like laptops, desktop computers, tablets, or mobile phones, intending to release additional malicious code like a virus, ransomware, or spyware. Hackers may use malware for many reasons. By using a destructive virus or ransomware, malware can sabotage the productivity of a […]
The Definition of Phishing

Phishing is a sort of online fraud. The fraudster approaches a target or targets via email, phone call, or text message pretending to represent a reliable institution to trick people into disclosing sensitive information. It includes passwords, banking and credit card information, and personally identifiable information. The goal is frequently to get you to visit […]
Is Your Computer on Its Last Legs?

If your computer is acting up or keeps breaking down, you might think of buying a new one. But if the problem is with the hardware, it may be possible to fix it. It might be possible to fix it easily and for much less money. This is also the best choice for the environment. […]
Five Common Warning Signs of Malware on Your Computer

Malware viruses are so common in the news that most of us know how bad they can be for businesses that have broken securities. Even so, most of us have had malware infection at some point in our careers. If we’re lucky, the virus has been more of a bother than anything else. Malware, on […]
